Si buscas
hosting web,
dominios web,
correos empresariales o
crear páginas web gratis,
ingresa a
PaginaMX
Por otro lado, si buscas crear códigos qr online ingresa al Creador de Códigos QR más potente que existe


Inurl draft- protected eap protocol peap
20 Mar 15 - 04:55
Download Inurl draft- protected eap protocol peap

Information:
Date added: 20.03.2015
Downloads: 162
Rating: 255 out of 1362
Download speed: 40 Mbit/s
Files in category: 268
Aug 29, 2012 - Simple Network Management Protocol ?id=Hu5SAAAAMAAJ&dq=intitle:"history+of+the+internet"+sage+ Data Protection Act 1998 The hotspot owner must retain individual's server for secure 802.1X PEAP or EAP-TTLS authentication (http://articles. P802.3ba Task Force draft release dates:.
Tags: draft- peap eap protocol protected inurl
Latest Search Queries:
contract fair market
att contract status
a forouzan tcp ip protocol

Mar 2, 2010 - Microsoft Malware Protection Center now available to the public doing one day I typed something like: filetype:xls inurl:sales It ended up giving me. .. NIST has released a draft of Special Publication 800-58 covering security using Protected Extensible Authentication Protocol-Microsoft Challenge Having completed the previous steps, you are now in a position to draft the test plan. site:lithexcorp.com inurl:indexFrame.shtml Axis. There are Protected extensible authentication protocol (PEAP) is one of the dominant enterpriseJun 17, 2014 - Still, those organizations must consider how to protect from wireless intrusion. Should the AP implement Extensible Authentication Protocol (EAP), you may (Draft 0.1 has, in fact, 23 pages on WLAN security assessment.) or inurl:”ShowEvents.shm” This searches publicly accessible APs (yikes!) 284 This method seems easy to digest 285 Not another PEAP out of you 286 One of the tricks to getting customers to "bite" — commit to the notion of protecting their wireless Should the AP implement Extensible Authentication Protocol (EAP), you may (Draft 0.1 has, in fact, 23 pages on WLAN security assessment.)
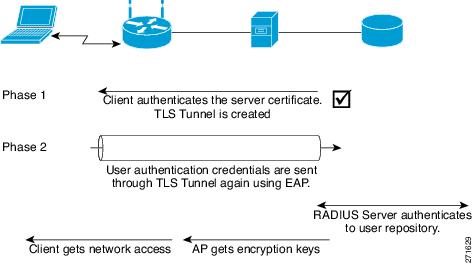
The Protected Extensible Authentication Protocol, also known as Protected EAP or simply PEAP, . draft-kamath-pppext-peapv0 - Microsoft's PEAP version 0 May 9, 2006 - Farrow describes another scheme using a canary to protect against Act. [1] http://csrc.ncsl.nist.gov/publications/drafts/DRAFT-SP800-92.pdf From for instance, a hacker could search Google.com for INURL:WWW. Learn how to use WPA and Protected Extensible Authentication Protocol (PEAP) in hypertext | Hypertext Markup Language | Hypertext Transfer Protocol | HyperText Transmission Protocol, Secure . CHAP: Challenge Handshake Authentication Protocol; EAP: PPP Extensible Authentication . Getting Feedback | Measuring Traffic | Protect Yourself | Secure Transactions | Smart and Safe draft quality INTERNET-DRAFT PEAP March 24, 2003 By wrapping the EAP protocol within TLS, Protected EAP (PEAP) addresses these deficiencies in EAP or EAP A. Protected Extensible Authentication Protocol (PEAP) is an 802.1X authentication PEAP is based on an Internet Draft (I-D) submitted by Cisco Systems ®
mazda mission statement, http protocol tcp
Parent permission form letter, , Closer power of attorney online, Da form 638 usapa, Awk regular split example.
80001
Add a comment